Select a firewall.
One of the most critical computer protection tools is a firewall, also called a firewall. It is a kind of gatekeeper that exercises strict control over incoming and outgoing data packets and has a set of rules for allowing programs and services into and out of the network. Surprisingly, firewalls are still not installed or configured properly on many computers. Meanwhile, a user whose PC is connected to the Internet and is not protected by a firewall puts both the performance of his machine and the safety of information at great risk. It’s even worse when the installed tool is configured incorrectly or when several firewalls are active on the PC at the same time, as a result of which both simple errors in the operation of the program and connection installation, and critical errors in the operation of the OS can occur. Some users have a bad attitude towards firewalls for the sole reason that when training mode is turned on, in the initial stages of operation, these protection tools display many requests to allow the traffic of applications trying to transmit or receive data from the Network. If you refuse such a request from a program, it will subsequently simply not connect to the Internet. On the other hand, allowing an unfamiliar utility to connect means exposing your PC to the risk of infection or data leakage. Even with minimal knowledge of setting up a firewall, such problems can be solved in a few seconds. However, the myth about the difficulty of debugging a firewall still persists. CHIP will talk about the basic principles of operation and configuration of firewalls and introduce the most popular software packages.
How firewalls work
The English name “firewall” and the German name “Brandmauer” hide the essence of the action of firewalls. Literally translated, they consist of two words: “wall” and “fire.” Initially, the term was used by firefighters to refer to special structures that can be used to protect adjacent buildings from the spread of fire. If we imagine that various network attacks are a fire, and the PC and home or office network are our home, then the purpose of such programs becomes obvious. In the case of a computer, the firewall takes on the role of a border checkpoint that allows network traffic to pass through and, in accordance with a list of rules, discards prohibited information, and also, depending on the settings, logs attempts at attacks from outside and unauthorized access to the Network. In this case, the user can set the rules for the operation of his “border point”. When creating such rules, depending on the firewall used, parameters such as protocol, address, port number, program name, rule operating time, actions in case of an attempt to establish a connection, and many other settings can be specified.
What are they like?
Modern firewalls can be divided into several types, each of which has pros and cons.
SOFTWARE- special applications that perform the role of a firewall and, as a rule, related security functions. Such tools are relatively easy to install and configure, but they are susceptible to virus attacks. For example, with rare updates to the system, antivirus and its databases, software firewalls may be disabled or partially damaged by malicious utilities. Unfortunately, the software comes at the cost of CPU and RAM load, which can be very noticeable on a low-power computer.
HARDWARE- professional, rather difficult to configure and expensive devices that relieve the PC load and are almost resistant to virus attacks. In addition, the operation of hardware firewalls can be invisible to the user and software, and their performance is much higher. Such devices are typically designed to filter traffic and protect the entire network, rather than individual PCs. They allow you to scan traffic for malicious and prohibited content and can be equipped with security add-ons.
HYBRID are firewalls built into various software and hardware products. They are used as an addition to antiviruses, proxy servers, modems, routers, access points, etc. Typically, such hardware allows you to make the most necessary settings and create several traffic filtering rules, which, however, may be quite sufficient for a home network .
Windows Firewall: Entry Level
Website: microsoft.ru; Price: for free
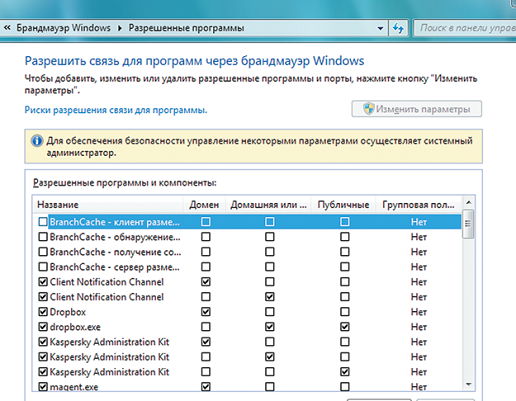
This firewall supports the simultaneous operation of several network profiles: domain - domain network in the organization; public - public (public and wireless) networks; home - home or work closed networks. Thus, the appropriate level of security is ensured for each case - for example, internal and virtual networks and Internet access. In "seven", the firewall user interface in the Control Panel has become more informative. For each active profile, additional information about the current settings is displayed. Two links have appeared on the left side of the Firewall Control Panel where you can change the settings for notifications about program blocking and enable or disable the firewall. Conveniently, for each profile, the function of blocking all incoming connections is available. In addition, you can add a program to firewall exceptions - this function is displayed on the left side of the dialog box. If you need to configure permissions for a specific utility, click on the “Allow a program or component to run...” link. To add an application to the list, you must click on “Allow another program”.
Outpost firewall PRO: comprehensive defense
Website: agnitum.ru; Price: from 899 rub.
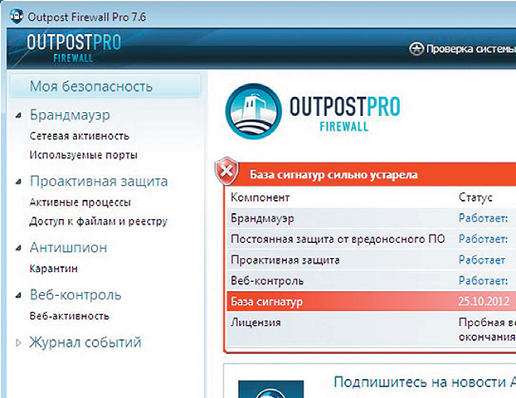
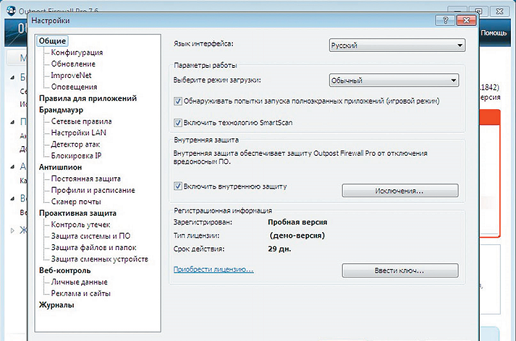
This product stands out for its well-thought-out interface with full support for the Russian language and an extensive set of protection tools when working in networks. At the same time, due to the large number of parameters, it will be more difficult for beginners to master it. It is possible to connect additional modules and fine-tune the program itself, as well as access to the Application Network: add and remove basic programs, set general rules and change utility policies. The package is designed in such a way that all basic firewall operations, such as ad blocking, content filtering, email filtering, and an attack detector, are assigned to plugins. The main module monitors network activity and the behavior of applications available in the system, and configures all its components. The program can operate in automatic mode or training mode. This is convenient when catching Trojans and spies. The package also includes a plugin for blocking online advertising. In this case, the program uses the “invisibility” mode by default, which makes it difficult to detect the user’s PC. and attacks on him. The utility is also equipped with a self-defense mechanism: when the outpost.exe process is deleted, communication with the Network is blocked.
Comodo firewall: friendly guardianship
Website: personalfirewall.comodo.com; Price: for free
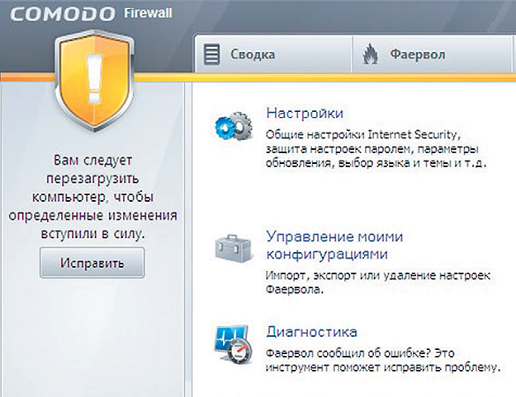
Perhaps the most friendly and simple utility, which at the same time offers ample opportunities and flexibility in configuration. In addition to the basic functions, this firewall allows you to view running processes, is equipped with a proactive protection module and can run applications in sandbox mode. For example, programs that are not recognized as trusted will only automatically run in isolation. Comodo also offers a convenient system of access rules for Internet applications and flexible control over the activities of software components. The program is automatically configured to work with DLL libraries, which are often used by keyloggers, Trojans and spyware to inject themselves into trusted processes. Application Behavior Analyzer monitors applications for modifications by third-party processes and other suspicious activity. Comodo Firewall constantly monitors its configuration files and blocks changes. However, password protection of settings is not provided. At times of peak activity, Comodo puts a lot of stress on the system. It is also too straightforward: for example, after blocking an allowed application under the guise of which a Trojan wanted to sneak in, you can use the program again only after a reboot.
Kerio WinRoute Firewall: professional, expensive
Website: winroute.ru; Price: OK. 10,000 rub. (for 5 PCs)
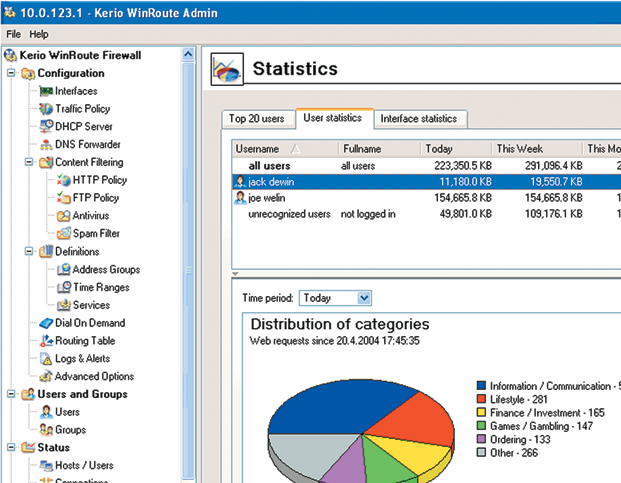
This package is actually not so much a firewall as it is a combination of this tool and a proxy server. With such focus and functionality, this program is not necessary for every home or even office network, and even more so, it is not very profitable to use this tool to protect and control the traffic of only one PC. It will be difficult for an untrained user to immediately understand the settings of this complex, but by spending some time studying the utility, you will be able to greatly strengthen the security and control of the entire network. Kerio WinRoute Firewall allows you to connect anti-virus modules to scan all passed information; configure Internet access rights for different users and PCs (including by time and traffic consumption); adjust the Internet connection speed for each group or user separately; view logs with the history of visits by users of the controlled local network to various resources.
The program requires a fairly significant amount of resources to operate, especially when used on a large, busy network. It is best to allocate a separate PC for Kerio WinRoute Firewall and create a so-called gateway.
Kaspersky Internet Security: all included
Website: kaspersky.ru; Price: 1600 rub.
This is a comprehensive antivirus package that includes a very powerful and functional firewall. Immediately after installation, it is ready to work and does not require special settings or training. The developers took care of the user’s nerves and drew up rules in advance for working on the Network with standard Windows services and typical applications. Also, by default, the application already keeps all critical ports closed, through which attacks from the Internet are possible. When detected, the module blocks the attacking host for a specified time, which can be configured. There is also a training mode in which you can describe in detail the allowed network activity of each program. If careful configuration is not required, there is a built-in set of standard rules that can be edited. Professionals will appreciate the selective blocking of Java applets, Java and VBS scripts, and ActiveX elements, the vulnerabilities of which are often exploited by attackers. When launching applications, the anti-virus package automatically checks their integrity and blocks them if modifications are detected. For inexperienced users, KIS has visual indicators that display open ports, a graph of application network activity, and count traffic.
Expert's word. Antivirus plus firewall

Without a firewall, the effectiveness of all other protection methods will certainly be reduced. A typical case when the use of a firewall is mandatory is when a PC is running on a public network, for example in a cafe. It is also extremely useful when used in large networks, as it allows you to filter out unnecessary data and requests and thus improve performance. Modern security packages take a multi-layered approach to protecting user transactions and data. All components, such as firewall, antivirus, application control, exploit protection, banking protection, etc., constantly exchange information with each other about decisions made and processes occurring on the computer. Therefore, it is important to use an antivirus and firewall from the same manufacturer, since, working together, they will provide a better level of protection than components from different companies. Beginners can gain initial knowledge about the capabilities of a modern firewall (for example, part of Kaspersky Internet Security) in the “Support” section on the manufacturer’s website: support.kaspersky.ru/8051.
How to check the firewall
After installing and configuring the firewall, you should check its effectiveness. Otherwise, the activity of the firewall may be harmful rather than beneficial. The use of special sites can help in solving this problem - such as, for example, 2ip.ru/checkport, portscan.ru, pcflank.com/test.htm, tools-on.net/privacy.shtml?2. In addition, CHIP recommends using test programs (Leak test): AWFT, PCFlank Leak test, 2ip Firewall tester or other similar ones. You can also use vulnerability scanners such as XSpider, eEye Retina Network Security Scanner, Nmap, or run one of them on one of the computers on your network and scan the internal range of IP addresses of the local network you are protecting.
