How to encrypt any data. Part 1
Nowadays, small businesses often neglect information security. Large corporations usually have their own IT departments, powerful technical support and advanced hardware.
Small companies typically rely on consumer software, which can have significant data security flaws. However, information in small organizations is also very important and needs to be fully protected.
Data encryption– an excellent tool for maintaining the safety of valuable information when transmitting data over the Internet, backing up on cloud servers, or when storing information on a laptop that is about to be checked at the airport.
Data encryption prevents anyone other than you and your legal representative from viewing sensitive information. Most programs used in offices and home computers have built-in tools for data encryption. In this article we will look at where to find them and how to use them.
A little about passwords
Any discussion of encryption methods should begin with a completely different topic - password complexity. Most data encryption methods require you to enter a password for subsequent encryption and decryption when viewed again. If you use a weak password, an attacker will be able to guess it and decrypt the file, which will defeat the whole purpose of encryption.A complex password should be at least 10 characters long, 12 characters is much better. It must include a random sequence of uppercase letters, lowercase letters, numbers and symbols. If you find it more convenient to remember letters, use a password of 20 characters or more, and it will be secure in this case.
If you are not sure about the security of your password, use the Secure Password Check online utility from Kaspersky to check.
Full logical drive encryption
Most Windows users protect their account with a password. This action will not protect your data if your computer or hard drive is stolen. An attacker will be able to directly access the data on the hard drive through another OS. If you store a large amount of important confidential data, it is best to use full disk encryption to protect against device theft.Microsoft's BitLocker tool makes it very easy to encrypt an entire hard drive if two conditions are met:
1. You are an Ultimate or Enterprise license holder for Windows 7 or Vista, or a Pro or Enterprise license for Windows 8
2. Your computer is equipped with a TRM (Trusted Platform Module) chip - a special cryptoprocessor containing cryptographic keys for protection
To check for TRM, run BitLocker. Windows will automatically inform you if this module is missing when you try to enable encryption. To activate BitLocker follow Control Panel -> System and Security -> BitLocker Drive Encryption or search for "Bitlocker" on Windows 8.
From the Bitlocker main menu, select the “Enable BitLocker” option next to the drive you want to encrypt. If your PC does not meet BitLocker requirements, you can still use programs or DiskCryptor to encrypt entire partitions (more information about encryption methods using TrueCrypt can be found in the second part of the article).
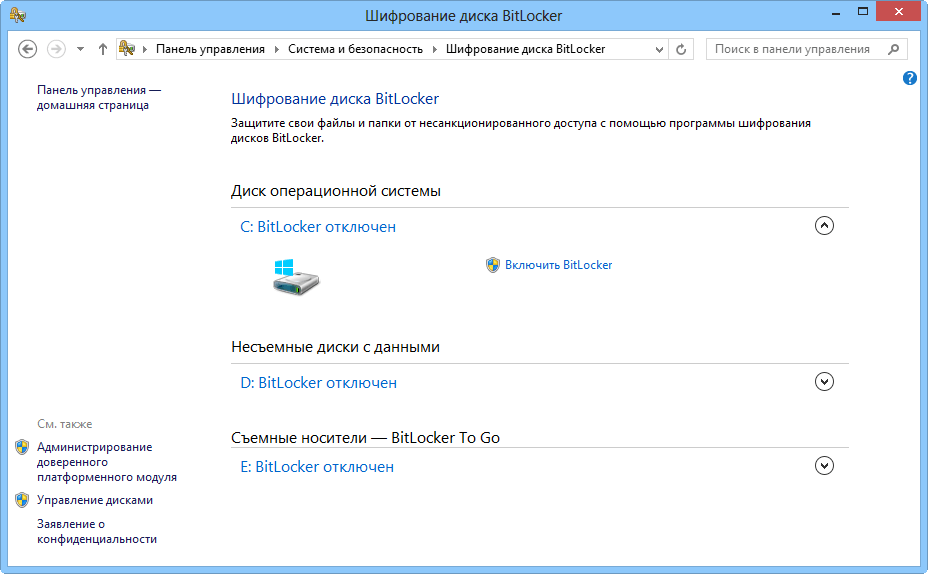
Encrypt external hard drives and USB drives
To fully encrypt flash drives and portable hard drives, you can use the Bitlocker To Go tool, which is specially designed for portable devices. To work, you also need Pro and Enterprise licenses of the operating system, but the TRM module is no longer required.To successfully perform encryption, simply insert the device, go to the BitLocker menu and at the bottom of the window, select the “Enable BitLocker” option next to the icon of the desired storage medium.
Internet traffic encryption
Sometimes you need to encrypt incoming and outgoing Internet traffic. If you work using an insecure Wi-Fi connection (for example, at an airport), an attacker could intercept sensitive data from your laptop. To prevent this possibility, you can use encryption using VPN technology.A virtual private network creates a secure “tunnel” between your computer and a secure third-party server. Data passing through this “tunnel” (both outgoing and incoming information) is encrypted, which will make it secure even if intercepted.
There are many VPNs available now with low monthly usage fees (such as Comodo TrustConnect or CyberGhost VPN). You can also set up your own private network for personal or business needs. The process of selecting and setting up a VPN is quite lengthy; we will not dwell on it in more detail.
Encrypting data on cloud servers, such as Dropbox
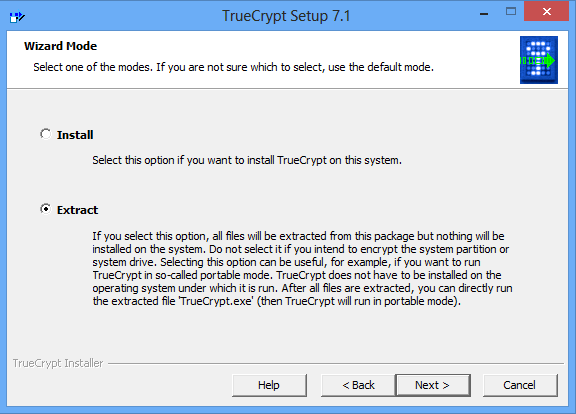
If you use Dropbox or SugarSync, we hasten to please you - these services have built-in tools for automatically encrypting data to protect it while moving or storing on servers. Unfortunately, these services also contain keys for decrypting data; this necessity is dictated by law.If you store confidential information in online services, use an additional level of encryption to protect your data from prying eyes. The most effective method is to use TrueCrypt to create an encrypted volume directly inside your Dropbox account.
If you want to access data from other computers, simply download the portable version of TrueCrypt to your Dropbox storage. For these purposes, when installing the TrueCrypt program menu, select the “Extract” option and specify the location in your online storage.
How to encrypt any data. Part 2...
Found a typo? Highlight and press Ctrl + Enter
