The files are encrypted by a virus, what should I do?
These viruses may differ slightly, but in general, their actions are always the same:
- install on your computer;
- encrypt all files that may have any value (documents, photographs);
- when trying to open these files, require the user to deposit a certain amount into the attacker’s wallet or account, otherwise access to the contents will never be opened.
The virus encrypted files in xtbl
Currently, a virus has become quite widespread, capable of encrypting files and changing their extension to .xtbl, as well as replacing their name with completely random characters.
In addition, a special file with instructions is created in a visible place readme.txt. In it, the attacker confronts the user with the fact that all his important data has been encrypted and now cannot be opened so easily, adding that in order to return everything to its previous state, it is necessary to perform certain actions related to transferring money to the fraudster (usually Before doing this, you need to send a specific code to one of the suggested email addresses). Often such messages are also supplemented with a note that if you try to decrypt all your files yourself, you risk losing them forever.
Unfortunately, at the moment, no one has officially been able to decrypt .xtbl; if a working method appears, we will definitely report about it in the article. Among the users there are those who had a similar experience with this virus and they paid the scammers the required amount, receiving in return a decryption of their documents. But this is an extremely risky step, because among the attackers there are also those who will not bother too much with the promised decryption; in the end, it will be money down the drain. 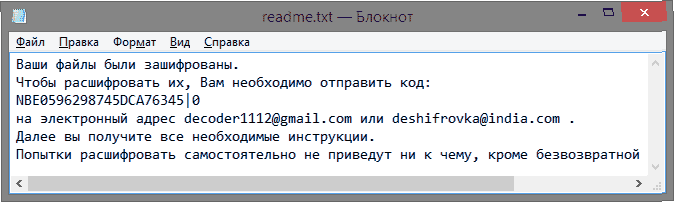
What to do then, you ask? We offer some tips that will help you get back all your data and at the same time, you will not follow the lead of scammers and give them your money. And so what needs to be done:
- If you know how to work in the Task Manager, then immediately interrupt file encryption by stopping the suspicious process. At the same time, disconnect your computer from the Internet - many ransomware require a network connection.
- Take a piece of paper and write down on it the code proposed to be sent by email to attackers (the piece of paper is because the file in which you will write may also become unreadable).
- Using Malwarebytes Antimalware, trial Kaspersky IS Anti-Virus or CureIt, remove the malicious program. For greater reliability, it is better to consistently use all the proposed means. Although you don’t have to install Kaspersky Anti-Virus if the system already has one main antivirus, otherwise software conflicts may arise. All other utilities can be used in any situation.
- Wait until one of the antivirus companies develops a working decryptor for such files. Kaspersky Lab does the job most quickly.
- Additionally, you can send to [email protected] a copy of the file that was encrypted, with the required code and, if available, the same file in its original form. It is quite possible that this could speed up the development of a file decryption method.
Do not under any circumstances:
- renaming these documents;
- changing their extension;
- deleting files.
 These Trojans also encrypt user files with subsequent extortion. In this case, encrypted files may have the following extensions:
These Trojans also encrypt user files with subsequent extortion. In this case, encrypted files may have the following extensions:
- .locked
- .crypto
- .kraken
- .AES256 (not necessarily this Trojan, there are others that install the same extension).
- .codercsu@gmail_com
- .oshit
- And others.
Fortunately, a special decryption utility has already been created - RakhniDecryptor. You can download it from the official website. 
On the same site you can read instructions that clearly and clearly show how to use the utility to decrypt all the files that the Trojan has worked on. In principle, for greater reliability, it is worth excluding the option to delete encrypted files. But most likely, the developers did a good job creating the utility and the integrity of the data is not in danger.
Those who use licensed Dr.Web antivirus have free access to decryption from the developers http://support.drweb.com/new/free_unlocker/.
Other types of ransomware viruses
Sometimes you may come across other viruses that encrypt important files and extort payment to return everything to its original form. We offer a small list of utilities to combat the consequences of the most common viruses. There you can also familiarize yourself with the main signs by which you can distinguish one or another Trojan program.
In addition, a good way would be to scan your PC with Kaspersky antivirus, which will detect the uninvited guest and assign a name to it. By this name you can already search for a decoder for it.
- Trojan-Ransom.Win32.Rector- a typical ransomware encryptor that requires you to send an SMS or perform other actions of this kind, we take the decryptor from this link.
- Trojan-Ransom.Win32.Xorist- a variation of the previous Trojan, you can get a decryptor with instructions for its use.
- Trojan-Ransom.Win32.Rannoh, Trojan-Ransom.Win32.Fury– there is also a special utility for these guys, look at
