Six myths about DDoS and one look from the inside
Increasingly, here and there in official communications from hosting providers there are references to reflected DDoS attacks. Increasingly, users, upon discovering the inaccessibility of their site, immediately assume DDoS. Indeed, in early March, the Runet experienced a whole wave of such attacks. At the same time, experts assure that the fun is just beginning. It is simply impossible to ignore a phenomenon so relevant, menacing and intriguing. So today let's talk about myths and facts about DDoS. From the hosting provider's point of view, of course.
Memorable day
On November 20, 2013, for the first time in the 8-year history of our company, the entire technical platform was unavailable for several hours due to an unprecedented DDoS attack. Tens of thousands of our customers throughout Russia and the CIS suffered, not to mention ourselves and our Internet provider. The last thing the provider managed to record before the white light faded for everyone was that its input channels were tightly clogged with incoming traffic. To visualize this, imagine your bathtub with a regular drain, with Niagara Falls rushing into it.
Even providers higher up the chain felt the effects of this tsunami. The graphs below clearly illustrate what was happening that day with Internet traffic in St. Petersburg and in Russia. Note the steep peaks at 15 and 18 hours, exactly at the moments when we recorded the attacks. For these sudden plus 500-700 GB.
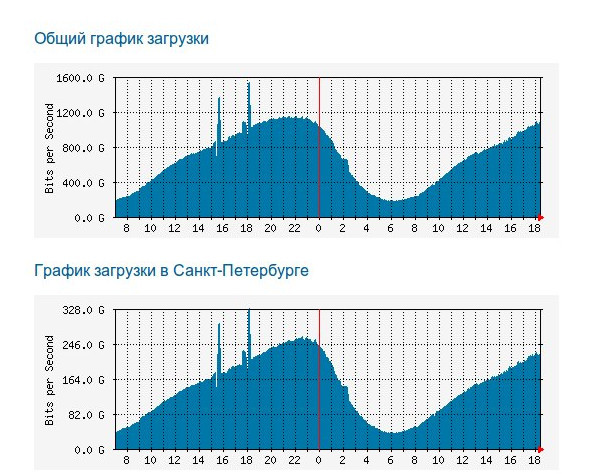
It took several hours to localize the attack. The server on which it was sent was calculated. Then the target of Internet terrorists was calculated. Do you know who all this enemy artillery was hitting? One very ordinary, modest client site.
Myth number one: “The target of the attack is always the hosting provider. This is the machinations of his competitors. Not mine." In fact, the most likely target of Internet terrorists is an ordinary client site. That is, the site of one of your hosting neighbors. Or maybe yours too.
Not everything is DDoS...
After the events on our technical site on November 20, 2013 and their partial repetition on January 9, 2014, some users began to assume DDoS in any particular failure of their own website: “This is DDoS!” and “Are you experiencing DDoS again?”
It is important to remember that if we are hit by such a DDoS that even our clients feel it, we immediately report it ourselves.
We would like to reassure those who are in a hurry to panic: if there is something wrong with your site, then the probability that it is DDoS is less than 1%. Simply due to the fact that a lot of things can happen to a site, and these “many things” happen much more often. We will talk about methods for quick self-diagnosis of what exactly is happening with your site in one of the following posts.
In the meantime, for the sake of accuracy of word usage, let’s clarify the terms.
About terms
DoS attack (from English Denial of Service) - This is an attack designed to cause a server to be denied service due to its overload.
DoS attacks are not associated with damage to equipment or theft of information; their goal - make the server stop responding to requests. The fundamental difference between DoS is that the attack occurs from one machine to another. There are exactly two participants.
But in reality, we see virtually no DoS attacks. Why? Because the targets of attacks are most often industrial facilities (for example, powerful productive servers of hosting companies). And in order to cause any noticeable harm to the operation of such a machine, much greater power is needed than its own. This is the first thing. And secondly, the initiator of a DoS attack is quite easy to identify.
DDoS - essentially the same as DoS, only the attack is distributed nature. Not five, not ten, not twenty, but hundreds and thousands of computers access one server simultaneously from different places. This army of machines is called botnet. It is almost impossible to identify the customer and the organizer.
Accomplices
What kind of computers are included in the botnet?
You will be surprised, but these are often the most ordinary home machines. Who knows?.. -
quite possibly your home computer carried away to the side of evil.
You don't need much for this. An attacker finds a vulnerability in a popular operating system or application and uses it to infect your computer with a Trojan that, on a certain day and time, commands your computer to begin performing certain actions. For example, send requests to a specific IP. Without your knowledge or participation, of course.
Myth number two: « DDoS is done somewhere far from me, in a special underground bunker where bearded hackers with red eyes sit.” In fact, without knowing it, you, your friends and neighbors - anyone can be an unwitting accomplice.
This is really happening. Even if you don't think about it. Even if you are terribly far from IT (especially if you are far from IT!).
Entertaining hacking or DDoS mechanics
The DDoS phenomenon is not uniform. This concept combines many options for action that lead to one result (denial of service). Let's consider the types of troubles that DDoSers can bring us.
Overuse of server computing resources
This is done by sending packets to a specific IP, the processing of which requires a large amount of resources. For example, loading a page requires executing a large number of SQL queries. All attackers will request this exact page, which will cause server overload and denial of service for normal, legitimate site visitors.
This is an attack at the level of a schoolchild who spent a couple of evenings reading Hacker magazine. She is not a problem. The same requested URL is calculated instantly, after which access to it is blocked at the web server level. And this is just one solution.
Overload of communication channels to the server (output)
The difficulty level of this attack is about the same as the previous one. The attacker determines the heaviest page on the site, and the botnet under his control begins to request it en masse.
Imagine that the part of Winnie the Pooh that is invisible to us is infinitely large
In this case, it is also very easy to understand what exactly is blocking the outgoing channel and prevent access to this page. Similar requests can be easily seen using special utilities that allow you to look at the network interface and analyze traffic. Then a rule is written for the Firewall that blocks such requests. All this is done regularly, automatically and so lightning fast that Most users are not even aware of any attack.
Myth number three: "A However, they rarely get through to my hosting, and I always notice them.” In fact, 99.9% of attacks you don't see or feel. But the daily struggle with them - This is the everyday, routine work of a hosting company. This is our reality, in which an attack is cheap, competition is off the charts, and not everyone demonstrates discernment in the methods of fighting for a place in the sun.
Overload of communication channels to the server (input)
This is already a task for those who read Hacker magazine more than one day.

Photo from the Ekho Moskvy radio website. We didn’t find anything more visual to represent DDoS with overloading of input channels.
To fill a channel with incoming traffic to capacity, you need to have a botnet, the power of which allows you to generate the required amount of traffic. But maybe there is a way to send little traffic and receive a lot?
There is, and not just one. There are many attack enhancement options, but one of the most popular right now is attack through public DNS servers. Experts call this amplification method DNS amplification(in case someone prefers expert terms). To put it simply, imagine an avalanche: a small effort is enough to break it, but inhuman resources are enough to stop it.
You and I know that public DNS server upon request, provides anyone with information about any domain name. For example, we ask such a server: tell me about the sprinthost.ru domain. And without hesitation, he tells us everything he knows.
Querying a DNS server is a very simple operation. It costs almost nothing to contact him; the request will be microscopic. For example, like this:
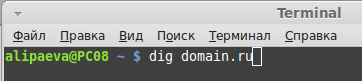
All that remains is to choose a domain name, the information about which will form an impressive package of data. So the original 35 bytes with a flick of the wrist turn into almost 3700. There is an increase of more than 10 times.
But how can you ensure that the response is sent to the correct IP? How to spoof the IP source of a request so that the DNS server issues its responses in the direction of a victim who did not request any data?
The fact is that DNS servers work according to UDP communication protocol, which does not require confirmation of the source of the request at all. Forging an outgoing IP in this case is not very difficult for doser. This is why this type of attack is so popular now.
The most important thing is that a very small botnet is enough to carry out such an attack. And several disparate public DNS, which will not see anything strange in the fact that different users from time to time request data from the same host. And only then will all this traffic merge into one stream and nail down one “pipe” tightly.
What the doser cannot know is the capacity of the attacker’s channels. And if he does not calculate the power of his attack correctly and does not immediately clog the channel to the server to 100%, the attack can be repulsed quite quickly and easily. Using utilities like TCPdump It’s easy to find out that incoming traffic is coming from DNS, and at the Firewall level, block it from being accepted. This option - refusing to accept traffic from the DNS - is associated with a certain inconvenience for everyone, however, both the servers and the sites on them will continue to operate successfully.
This is just one option out of many possible to enhance an attack. There are many other types of attacks, we can talk about them another time. For now, I would like to summarize that all of the above is true for an attack whose power does not exceed the width of the channel to the server.
If the attack is powerful
If the attack power exceeds the capacity of the channel to the server, the following happens. The Internet channel to the server is instantly clogged, then to the hosting site, to its Internet provider, to the upstream provider, and so on and on and on upward (in the long term - to the most absurd limits), as far as the attack power is sufficient.
And then it becomes a global problem for everyone. And in a nutshell, that's what we had to deal with on November 20, 2013. And when large-scale upheavals occur, it’s time to turn on special magic!

This is what the special magic looks like. Using this magic, it is possible to determine the server to which the traffic is directed and block its IP at the Internet provider level. So that it stops receiving any requests to this IP through its communication channels with the outside world (uplinks). For term lovers: experts call this procedure "blackhole", from English blackhole.
In this case, the attacked server with 500-1500 accounts remains without its IP. A new subnet of IP addresses is allocated for it, over which client accounts are randomly evenly distributed. Next, experts are waiting for the attack to repeat itself. It almost always repeats itself.
And when it repeats, the attacked IP no longer has 500-1000 accounts, but only a dozen or two.
The circle of suspects is narrowing. These 10-20 accounts are again distributed to different IP addresses. And again the engineers are in ambush waiting for the attack to repeat. Again and again they distribute the accounts remaining under suspicion to different IPs and thus, gradually approaching, determine the target of the attack. All other accounts at this point return to normal operation on the previous IP.
As is clear, this is not an instant procedure; it takes time to implement.
Myth number four:“When a large-scale attack occurs, my host has no plan of action. He just waits, with his eyes closed, for the bombing to end, and answers my letters with the same type of replies.”This is not true: in the event of an attack, the hosting provider acts according to a plan to localize it and eliminate the consequences as quickly as possible. And letters of the same type allow you to convey the essence of what is happening and at the same time save the resources necessary to deal with an emergency situation as quickly as possible.
Is there light at the end of the tunnel?
Now we see that DDoS activity is constantly increasing. Ordering an attack has become very accessible and outrageously inexpensive. In order to avoid accusations of propaganda, there will be no prooflinks. But take our word for it, it is true.

Myth number five: “A DDoS attack is a very expensive undertaking, and only business tycoons can afford to order one. At the very least, this is the machinations of the secret services!” In fact, such events have become extremely accessible.
Therefore, one cannot expect that malicious activity will disappear on its own. Rather, it will only intensify. All that remains is to forge and sharpen the weapon. This is what we do, improving the network infrastructure.
Legal side of the issue
This is a very unpopular aspect of the discussion of DDoS attacks, since we rarely hear about cases of the perpetrators being caught and punished. However, you should remember: A DDoS attack is a criminal offense. In most countries of the world, including the Russian Federation.
Myth number six: « Now I know enough about DDoS, I’ll order a party for a competitor - and nothing will happen to me for this!” It is possible that it will happen. And if it does, it won’t seem like much.
- The beginning of the story with DDoS of the Assist payment system
- Exciting ending
In general, we do not advise anyone to engage in the vicious practice of DDoS, so as not to incur the wrath of justice and not to ruin your karma. And we, due to the specifics of our activities and keen research interest, continue to study the problem, stand guard and improve defensive structures.
PS:we don't have enough kind words to express our gratitude, so we just say"Thank you!" to our patient customers who warmly supported us on a difficult day on November 20, 2013. You have said many encouraging words in our support in
