User Account Control (UAC) Guide
User Account Control is probably the most underrated and perhaps even the most hated feature that debuted in Vista and has been part of all subsequent versions of Windows. Much of the hate that users throw at User Account Control is, in my opinion, undeserved, since the feature provides real benefits. I completely agree that User Account Control (UAC) can be quite annoying at times, but it was introduced into Windows for a purpose. No, not to interfere with users, but to facilitate a smooth transition from a standard (restricted) account to an administrator account.
In this article, I'll explain what UAC is, how it works, why it's necessary, and how to configure it. I have no intention of telling you why you should use UAC, but rather informing you of what you're missing out on by disabling it.
A little background and account information
As you should know, Windows works with so-called accounts. They come in two types: administrator and standard (limited).
The administrator account gives the user full access to all functions of the operating system, i.e. the user can do whatever he wants. A standard account user has reduced rights and is therefore only allowed to do certain things. This, as a rule, is all that affects only the current user. For example: changing the wallpaper on the desktop, mouse settings, changing the sound scheme, etc. In general, everything that is specific to a specific user and does not apply to the entire system is available in the standard account. Anything that can affect the system as a whole requires administrator access.
One of the tasks assigned to these accounts is to protect against malicious code. The general idea here is that the user performs normal work under a limited account and switches to the administrator account only when an action requires it. Paradoxically, malware receives the same level of rights with which the user logged in.
In Windows 2000 and Windows XP, performing actions as an administrator is not implemented flexible enough, and therefore working under a limited account was not very convenient. One of the ways to perform an administrative action in these versions of the system looks like this: logging out of a limited account (or quick switching if you were using Windows XP) -> logging into the administrator account -> performing an action -> logging out of the administrator account (or quick switching if Windows XP was used) -> return to a limited account.
Another option is to use the context menu and the "Run as another user" option, which opens a window in which you must specify the appropriate administrator account and password to run the file as an administrator. This is a fairly quick way to switch from one account to another, but it does not apply to any situation that requires administrative privileges. Another problem with this method is that the administrator account must have a password, otherwise execution will fail.
That's why User Account Control was introduced in Windows Vista and brought to near perfection in Windows 7.
What is UAC
UAC is a feature in Windows Vista, 7, 8, 8.1 and 10 that aims to make the transition from a restricted environment to an administrator environment as smooth and hassle-free as possible, eliminating the need to manually run files as an administrator or switch between accounts. In addition, UAC is an additional layer of protection that requires little effort on the part of the user, but can prevent serious damage.
How UAC works
When a user logs into their account, Windows creates a so-called user access token, which contains certain information about that account and mainly various security identifiers that the operating system uses to control the access capabilities of that account. In other words, this token is a kind of personal document (like a passport, for example). This applies to all versions of Windows based on the NT kernel: NT, 2000, XP, Vista, 7, 8 and 10.
When a user logs into a standard (limited) account, a standard user token with limited rights is generated. When a user logs into an administrator account, a so-called. administrator token with full access. Logical.
However, in Windows Vista, 7, 8 and 10, if UAC is enabled and the user is logged into an administrator account, Windows creates two tokens. The Administrator one remains in the background, and the Standard one is used to launch Explorer.exe. That is, Explorer.exe runs with limited rights. In this case, all processes launched after this become subprocesses of Explorer.exe with inherited limited privileges of the main process. If a process requires administrative rights, it requests an administrator token, and Windows in turn asks the user for permission to provide the process with this token in the form of a special dialog box.
This dialog box contains the so-called secure desktop, which can only be accessed by the operating system. It looks like a darkened snapshot of the actual desktop and only contains an administrator confirmation window and possibly a language bar (if more than one language is activated).
If the user does not agree and clicks “No,” Windows will deny the process an administrator token. And if he agrees and selects “Yes,” the operating system will grant the process the privileges it needs, namely, an administrator token.
If the process is already running with reduced rights, it will be restarted with elevated (administrator) rights. A process cannot be demoted or promoted directly. Once a process has been launched with one token, it will not be able to obtain other rights until it is launched again with new rights. An example is the Task Manager, which always runs with limited rights. If you click the "Show processes of all users" button, Task Manager will be closed and launched again, but with administrator rights.
When using a standard account, UAC asks you to specify a specific administrator account and enter a password:
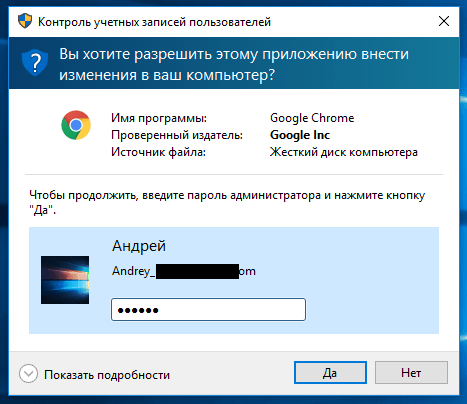
How UAC protects the user
UAC by itself does not provide much security. It just makes it easier to transition from a restricted environment to an administrative one. So a better way of asking the question is therefore how a restricted account hinders the user. Under a restricted user profile, processes cannot access certain system areas:
- main disk partition;
- other users' user folders in the \Users\ folder;
- Program Files folder;
- Windows folder and all its subfolders;
- sections of other accounts in the system registry
- HKEY_LOCAL_MACHINE section in the system registry.
Any process (or malicious code) without administrator rights cannot penetrate deep into the system, without access to the necessary folders and registry keys, and therefore cannot cause serious damage to the system.
Can UAC interfere with older programs that are not officially compatible with Vista/7/8/10
Should not. When UAC is enabled, virtualization is also enabled. Some old and/or simply poorly written programs do not use the correct folders to store their files (settings, logs, etc.). The correct folders are the folders in the AppData directory that each account has and where each program can create a folder to store whatever it wants.
Some programs try to save their files to Program Files and/or Windows. If the program is run with administrator rights, this will not be a problem. However, if the program is running with limited permissions, it will not be able to make changes to files/folders in Program Files and/or Windows. The operating system simply won't allow it.
In order to prevent problems with such programs, Windows offers virtualization of folders and registry keys that programs with limited rights cannot access in principle. When such a program tries to create a file in a protected folder, the operating system redirects it to a special VirtualStore folder, which is located in X:\Users\<имя-вашего-профиля>\AppData\Local\(where X: is the system partition, usually C:). Those. Through the eyes of the program itself, everything is fine. She faces no obstacles and feels like she creates files/folders exactly where she wants them. VirtualStore typically contains Program Files and Windows subfolders. Here is a screenshot of Program Files in my VirtualStore folder:
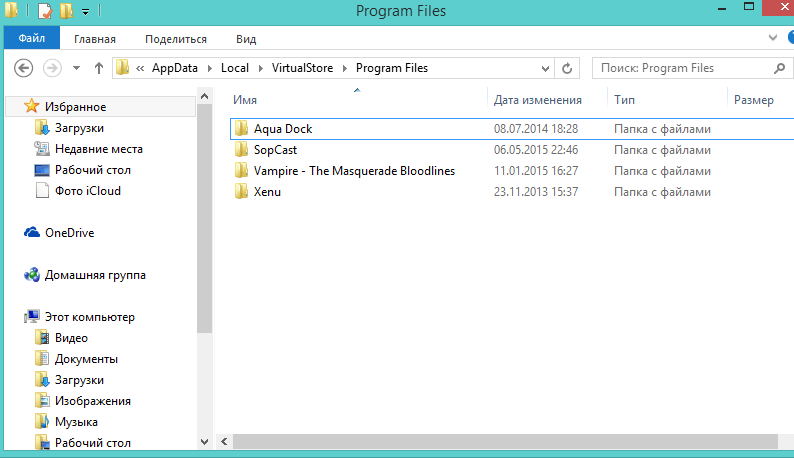
And here is what is in the SopCast folder, for example:
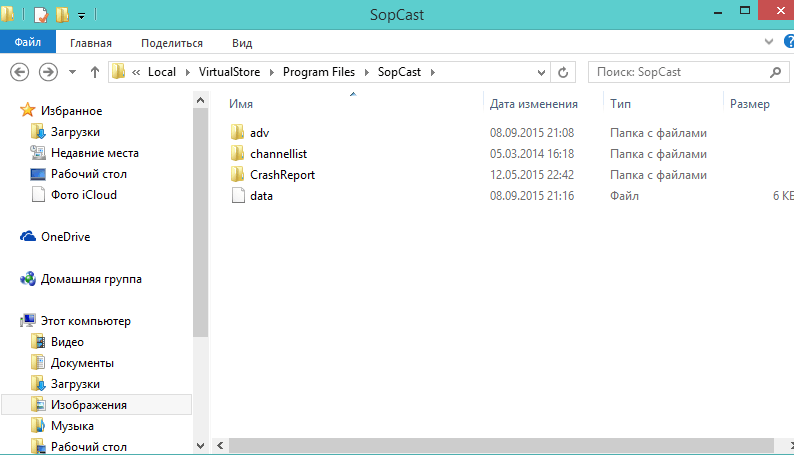
Those. if UAC was stopped, or the program was always run as administrator, these files/folders would be created in C:\Program Files\SopCast. In Windows XP, these files and folders would be created without problems, because all programs in it have administrator rights by default.
This, of course, should not be considered by developers as a permanent solution. The responsibility of each author is to create software that is fully compatible with current operating systems.
UAC Dialog Boxes
You may have noticed that there are only three different UAC dialog boxes. Here we will look at those in Windows 7, 8.x and 10. In Vista, the dialogs are somewhat different, but we will not dwell on them.
The first type of window has a dark blue stripe at the top and a shield icon in the upper left corner, which is divided into 2 blue and 2 yellow sections. This window appears when confirmation is required for a process with a digital signature that belongs to the operating system - the so-called. Windows binaries. We'll talk about them below.
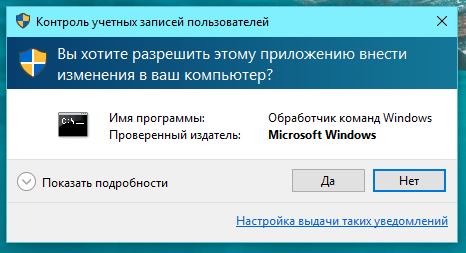
The second type of window also has a dark blue ribbon, but the shield icon is completely blue and has a question mark. This window appears when confirmation is required for a digitally signed process, but the process/file is not owned by the operating system.
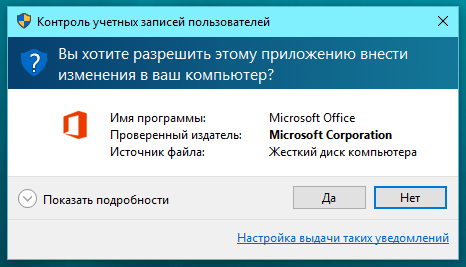
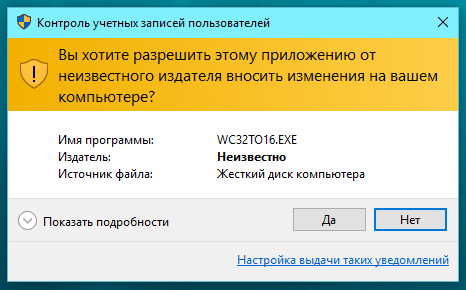
The third window is decorated with an orange stripe, the shield is also orange, but with an exclamation mark. This dialog appears when confirmation is required for a process without a digital signature.
UAC Settings
User Account Control settings (operating modes) are located in Control Panel -> System and Security -> Change User Account Control settings. There are only 4 of them:
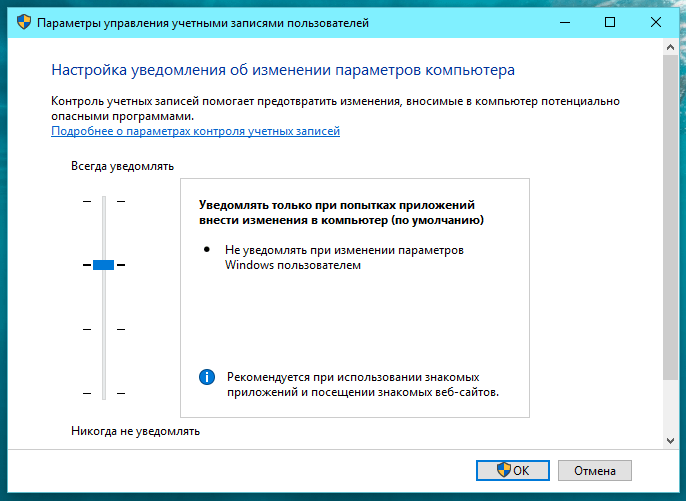
Always notify is the highest level. This mode is equivalent to the way UAC works in Windows Vista. In this mode, the system always requires confirmation of administrator rights, regardless of the process and what it requires.
The second level is the default in Windows 7, 8.x and 10. In this mode, Windows does not display the UAC window when it comes to the so-called Windows binaries. Those. If a file/process that requires administrator rights meets the following 3 conditions, the operating system will grant them to it automatically, without confirmation from the user:
- the file has a manifest built-in or as a separate file, which indicates automatic elevation of rights;
- the file is located in the Windows folder (or in any of its subfolders);
- the file is signed with a valid Windows digital signature.
The third mode is the same as the second (previous), but with the difference that it does not use a secure desktop. That is, the screen does not darken, and the UAC dialog box appears like any other. Microsoft does not recommend using this option, and I will explain why later.
Do not notify me is the fourth and final level. This essentially means disabling UAC completely.
Two remarks are in order here:
- The Windows digital signature refers specifically to the operating system. I say this because there are also files that have been digitally signed by Microsoft. These are two separate signatures, with UAC only recognizing the Windows digital signature as it acts as proof that the file is not only from Microsoft, but is part of the operating system.
- Not all Windows files have a manifest for automatic elevation of rights. There are files that deliberately lack this. For example, regedit.exe and cmd.exe. It is clear that the second one is deprived of automatic promotion, because it is very often used to launch other processes, and as already mentioned, each new process inherits the rights of the process that launched it. This means that anyone could use the Command Prompt to run any processes seamlessly with administrator rights. Fortunately, Microsoft is not stupid.
Why is it important to use a secure desktop?
A secure desktop prevents any possible interference and influence from other processes. As mentioned above, only the operating system has access to it and with it it only accepts basic commands from the user, that is, pressing the “Yes” or “No” button.
If you are not using a secure desktop, an attacker could spoof a UAC window to fool you into running their malicious file with administrator rights.
When are administrator rights needed? When does the UAC window appear?
In general, there are three cases in which UAC addresses the user:
- when changing system (not user) settings, although in fact this only applies to the maximum UAC level;
- when installing or uninstalling a program/driver;
- when an application/process requires administrator privileges to make changes to system files/folders or system registry keys.
Why it's important not to disable UAC
User Account Control provides a high level of protection, and requires virtually nothing in return. That is, the UAC efficiency is very high. I don't understand why he annoys people so much. In everyday work, the average user sees the UAC window 1-2 times a day. Maybe even 0. Is it that much?
The average user rarely changes system settings, and when they do, UAC does not bother with its questions if it works with the default settings.
The average user does not install drivers and programs every day. All drivers and most of the necessary programs are installed once - after installing Windows. That is, this is the main percentage of UAC requests. After this, UAC intervenes only when updating, but new versions of programs are not released every day, not to mention drivers. Moreover, many do not update either programs or drivers at all, which further reduces UAC issues.
Very few programs need administrator rights to do their job. These are mainly defragmenters, cleaning and optimization tools, some programs for diagnostics (AIDA64, HWMonitor, SpeedFan, etc.) and system settings (Process Explorer and Autoruns, for example, but only if you need to do something specific - say, disable a driver /service or program starting from Windows). And all these are programs that either need not be used at all, or in rare cases. All frequently used applications work absolutely fine with UAC and do not ask any questions:
- multimedia players (audio and/or video);
- video/audio converters;
- programs for image/video/audio processing;
- programs for capturing screenshots of your desktop or video recordings on it;
- image viewing programs;
- web browsers;
- file downloaders (download managers and clients of P2P networks);
- FTP clients;
- instant messengers or programs for voice/video communication;
- disc burning programs;
- archivers;
- text editors;
- PDF readers;
- virtual machines;
- and etc.
Even installing Windows updates does not use the UAC window.
There are people who are willing to sacrifice 1-2 or more minutes a day to "optimize" the system with some crookedly written programs that do nothing useful, but are not willing to spend a few seconds a day to respond to UAC requests.
Various statements like “I am an experienced user and I know how to protect myself” are not enough, because no one is immune and the outcome of certain situations does not always depend on the user. Moreover, people tend to make mistakes; it happens to everyone.
Let me give you one example: let's say you are using a program that has vulnerabilities, and one day you find yourself on a site that exploits those vulnerabilities. If User Account Control is enabled and the program runs with limited rights, an attacker will not be able to cause much trouble. Otherwise, the damage to the system can be colossal.
And this is just one of many examples.
Running applications alongside Windows with administrator rights
I admit that there may be users who turn off UAC simply to be able to run programs along with Windows and with administrator rights. This is not possible in the normal way because UAC cannot send a request to the user until the desktop is loaded. However, there is a way through which you can leave UAC enabled. Here he is:
- open Task Scheduler;
- click Create a task;
- in field Name enter something of your choice, and at the bottom of the window turn on the option Run with highest rights;
- go to the tab Triggers and press Create;
- Select from the drop-down menu at the top When you log in; if you want to create a task for a specific user, select the option User and then click Change user; enter your username and confirm by pressing the button OK;
- go to the tab Actions and press Create;
- click Review, indicate the appropriate application and confirm your choice;
- go to the tab Conditions and disable the option Run only on mains power;
- on the tab Options disable the Stop task that takes longer to complete option;
- confirm by pressing OK.
Ready. The task has been added so that the application will now load automatically with administrator rights. There is, however, one small catch here: all such tasks are performed with a priority lower than normal - below normal (below normal). If you're okay with that, then it's okay. If not, then you'll have to work a little harder:
- run Task Scheduler if you have already closed it;
- select Job Scheduler Library;
- mark your task, click Export and save it in .xml format;
- open the .xml file in a text editor;
- find the section
7 , which should be at the end of the file and change the seven (7) between the opening and closing tags to a five (5); - save the file;
- In the Task Scheduler, highlight your task again, click Delete and confirm the deletion;
- now click Import task, select the file you just saved and click the button OK.
That's all. Whether you use UAC or not is up to you, but it's important to know what you're losing when you disable it, as well as being aware of the risks. Thank you for your attention!
Have a great day!
